By Wayne Bennett – Sr Program Manager | Microsoft Endpoint Manager – Intune
Using Microsoft Endpoint Manager – Microsoft Intune to set your company’s terms and conditions meets the requirements of many organizations. However, the Azure Active Directory (Azure AD) terms of use feature offers greater functionality— including terms of use in different languages and integration with Conditional Access in the form of grant controls. You can learn more about the differences between the two solutions in this blog post.
Potential to block access to Intune
If you’ve configured the Azure AD terms of use solution and set a grant control to require users to accept terms of use in your Conditional Access policy, you need to be aware of a configuration scenario that might unintentionally block access for your users when they try to enroll into Intune.
Typical configuration
When creating an Azure AD terms of use policy, you have the option to select Require users to consent on every device. If you choose this setting, you will see the Consent on every device will require users to register each device with Azure AD prior to getting access warning. Once saved, you are unable to change this setting.

After you create the terms of use policy, the next step is to create a Conditional Access policy. As shown in the following example, many organizations will target All Cloud Apps without configuring any exclusions.
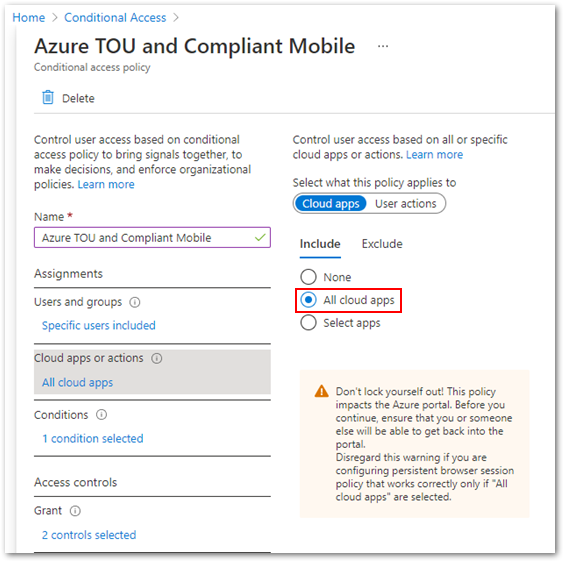
Additionally, many organizations will select Require device to be marked as compliantgrant controls and require users to accept the Azure AD terms of use policy.

Blocking enrollment issue
The combination of Azure AD terms of use requiring users to consent on every device, Conditional Access policy targeting All Cloud Apps, and the control requiring the user to accept the Azure AD terms of use results in the following unintended behaviour during the Intune enrollment process:
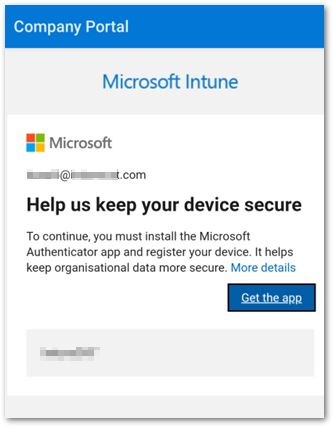
- Once the user has authenticated in the Company Portal, prior to Azure AD terms of use appearing, the Help us keep your device secure message will appear. The user will be prompted to install the Microsoft Authenticator app, Conditional Access controls will begin a continuous registration cycle, and the user will be unable to complete enrollment.
The issue is caused by selecting Require users to consent on every device, requiring users to register each device with Azure AD prior to getting access, as per the warning, when creating the terms of use policy.
Prevent Intune enrollment from being blocked
There are two methods to keep the enrollment blocking scenario from occurring:
Method 1: The Terms of use dialog
The first method is to ensure that Require users to consent on every device in the Terms of use dialog remains at the default Off setting when creating the Azure AD terms of use policy.
Note
Once the Azure AD terms of use policy is created, it is not possible to edit the Require users to consent on every device setting. You must create and target a new terms of use policy in the Conditional Access policy.
Method 2: Exclude cloud apps
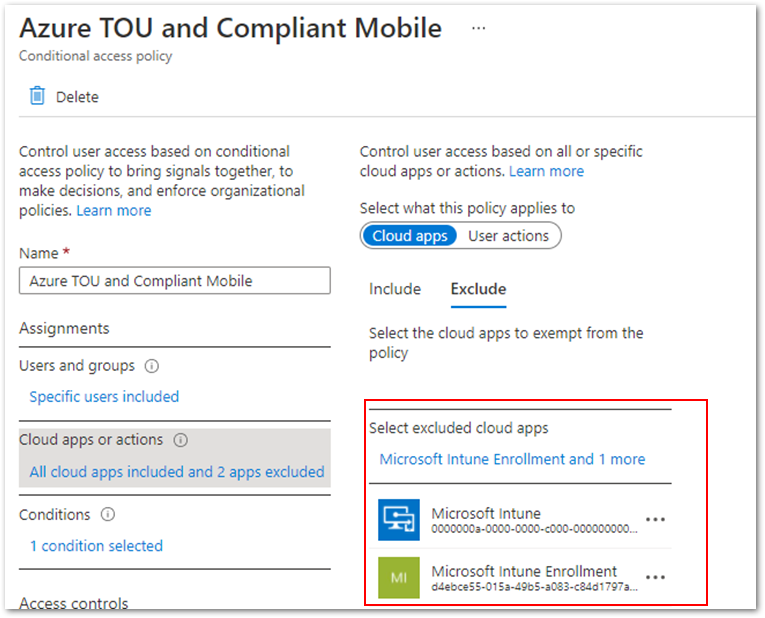
The second method is to exclude certain cloud apps from Conditional Access targeting. The Per-device terms of use section of the Azure Active Directory terms of use documentation states that “The Intune Enrollment app is not supported. Ensure that it is excluded from any Conditional Access policy requiring Terms of Use policy.” However, excluding the Microsoft Intune Enrollment cloud app is not sufficient— as the example below shows, you must also exclude the Microsoft Intune cloud app.
Conclusion
Changing your configuration using either of the suggested methods will prevent the Intune enrollment blocking scenario. Before you make any change, be sure to evaluate the settings so you don’t impact any existing Conditional Access requirements.
More info and feedback
For further resources on this subject, please see the links below.