Detect and remediate Windows Speculative Execution on Windows 10 machines using PowerShell and Proactive Remediation in Intune.
Within Intune there is the option to create remediation task, this is basically a PowerShell script that will run against the machine and exit with a 1 or a 0 if the condition is found.
With the Speculative Execution Check the remediation is to set registry setting to protect the machine.
Extra information can be found at the following Microsoft web page.
Detection Script
This is a Powershell script that exits with a 1 if the value is not as required. This will trigger the remediation script to be run.
<#=======================================================================================
Script Name: Detect_spectar_meltdown_Vulnerabilities.ps1
Description: Detect if the setting for the Itel processors have been applied to the registry
Notes: v1.0 – Remediate if exit is 1 is found, change as appropriate
v1.1 – Extra registry location added for Virtulization (Hyper-v enabled)
=======================================================================================#>
try {
$RegResult = Get-ItemProperty -Path “Registry::HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management”
If (-Not $RegResult.FeatureSettingsOverride -eq “72”) {
Write-Host “Match”
Exit 1
}
ElseIf (-Not $RegResult.FeatureSettingsOverrideMask -eq “3”) {
Write-Host “Match” Exit 1
}
else {
Write-Host “No_Match”
}
}
catch {
$errMsg = $_.Exception.Message
return $errMsg
Write-Host “Match”
exit 1}
try {
$RegResult = Get-ItemProperty -Path “Registry::HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization”
If (-Not $RegResult.MinVmVersionForCpuBasedMitigations -eq “1.0”) {
Write-Host “Match”
Exit 1
}
else {
Write-Host “No_Match”
}
}
catch {
$errMsg = $_.Exception.Message
return $errMsg
Write-Host “Match”
exit 1
}
Exit 0
Remediation Script
Remediation script is a simple registry change script. If the values do not exist they will just be created.
<#=======================================================================================
Script Name: Remediate_spectar_meltdown_Vulnerabilities.ps1
Description: This script updates the registry to protect from Spectar and Meltdown Vulnerabilities
Notes: v1.0 – No variable substitution needed
v1.1 – Extra registry location added for Hyper-V enabled machines
=======================================================================================#>
try {
Set-ItemProperty -Path “Registry::HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management” -Name FeatureSettingsOverride -Value 72
Set-ItemProperty -Path “Registry::HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management” -Name FeatureSettingsOverrideMask -Value 3
Set-ItemProperty -Path “Registry::HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization” -Name MinVmVersionForCpuBasedMitigations -Value 1.0
Exit 0
}
catch{
$errMsg = $_.Exception.Message
return $errMsg
exit 1
}
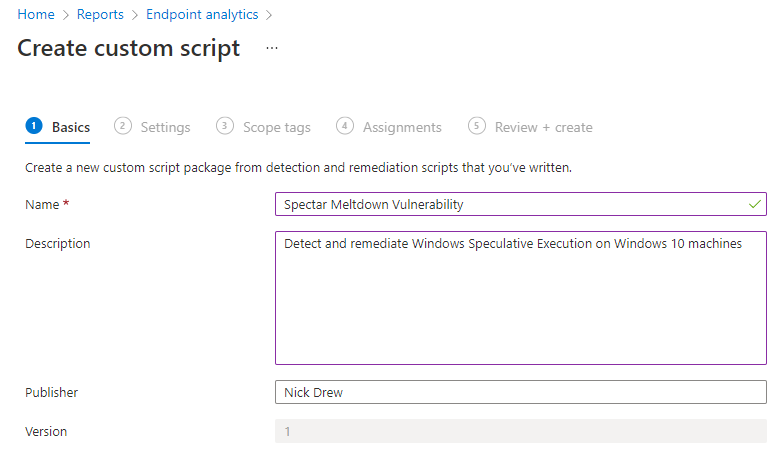
Create the Intune remediation
From within Intune go to Reports-Endpoint Analytics-Proactive Remediations.
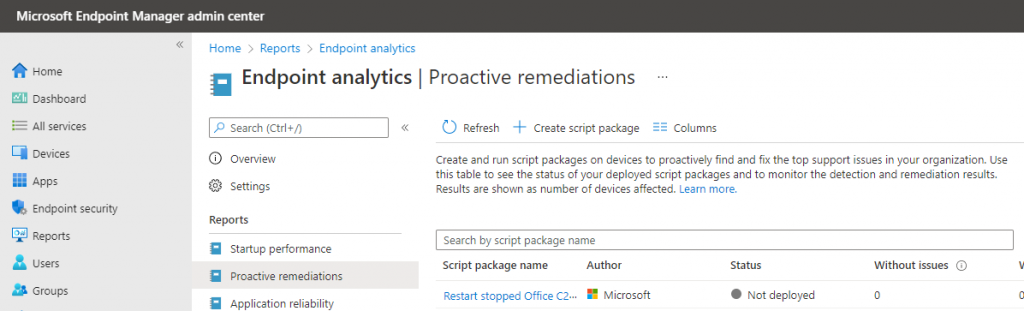
Select +Create script Package
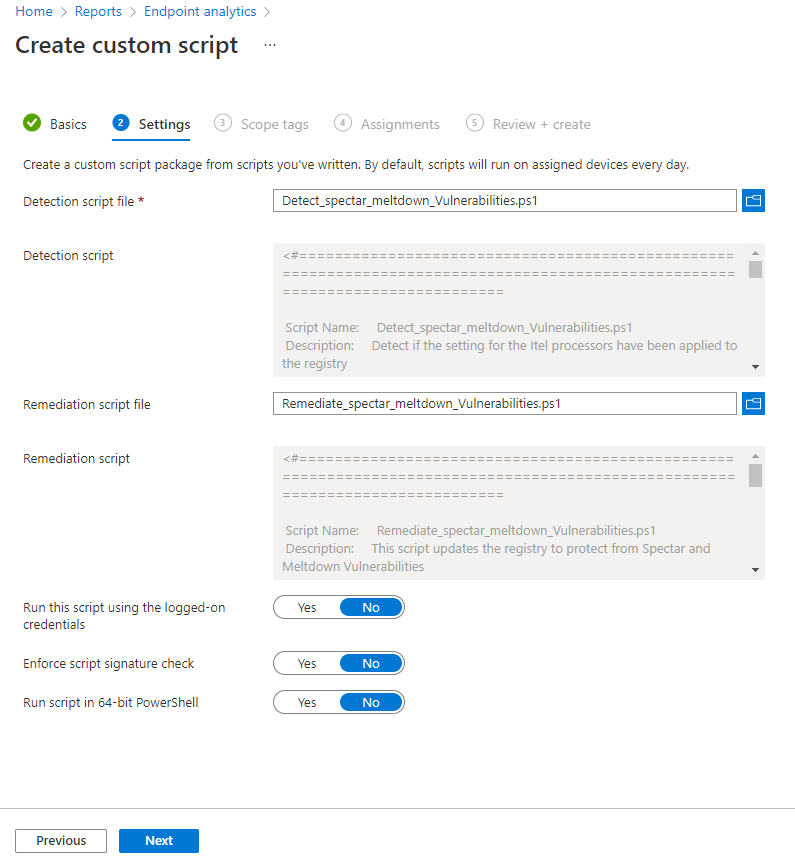
“Run this script using the logged-on credentials” – No
“Enforce script signature check” – No (Unless you have this enable, I do not)
“Runscript in 64-bit PowerShell” – No
Assign a scope if required